CurseForge is a popular modding platform which hosts thousands of Minecraft mods. Sadly, CurseForge was recently attacked by malicious users who posted mods containing an exploit which was named after the user who posted it, fractureiser.
Please read this article from top to bottom – the severity of this exploit might force you to reinstall your operating system. I am not kidding.
What Happened
Some popular Curseforge and dev.bukkit.org (not the Bukkit software itself) accounts were hacked, and malicious software was injected into many popular plugins and mods. According to fractureiser-investigation on GitHub, there are reports of malicious plugin/mod JARs as early as mid-April.
What Does “Fractureiser Malware” Do
While the investigation is not fully complete at this moment, there is evidence of the malware doing the following:
- Copy itself to all jar files on your operating system, possibly infecting mods that were not downloaded from CurseForge or BukkitDev, or other Java programs.
- Steal cookies and login information from your web browser
- Replace cryptocurrency addresses in the clipboard with the attacker’s own address (yay!)
- Steal Discord credentials
- Steal Microsoft and Minecraft credentials
It’s quite bad. We’re not often covering malware at MineAcademy but due to the severity we felt it was necessary.
Who Was Not Infected
If you only play vanilla Minecraft through the official launcher or Prism launcher, and have never touched any mods ever: you are 100% safe. Or, if you know you haven’t downloaded any of the projects listed below in the past month, you should be safe too.
Also note that Fractuireiser malware only affects Windows and Linux, not macOS.
A List Of Infected Mods
Last updated June 8th, 15:00 CEST.
The following is an extensive list based on the sources at the bottom of the article, namely prismlauncher.org and curseforge.com.
Infected mods that were fixed:
According to CurseForge, most of the projects from LunaPixelStudios were infected. Ensure that you have the latest version of any modpack, as the necessary fixes should already be available for those modpacks, and the infected files deleted.
- Better MC
- Buried Barrels
- Medieval MC
- Prominence
- Simply Houses
- Sky Villages
- Skyblock Core
- When Dungeons Arise
Mods that are infected and taken down permanently
- AmazingTitles
- Anti ChatReport
- AntiCommandSpam Bungeecord Support
- AntiCrashXXL
- AntiRedstoneCrash
- Autobroadcast
- Create: Diesel and Oil Generators
- Create Infernal Expansion Plus
- DisplayEntityEditor
- Dungeonx
- DungeonZ
- Easy Custom Foods
- Fragment Permission Plugin
- Golem Awakening
- HavenElytra
- hydrationPlugin
- McBounties
- McPvPCountdown (formerly known as MCBounties)
- More and Ore advanced
- Museum Curator Advanced
- NoVPN
- Phanerozoic Worlds
- Simple Frames
- Skelegram – The Skript Telegram Addon
- SimpleHarvesting
- The Nexus Event Custom Event
- Ultra Swords Mod
- UltimateLevels
- UVision ENHANCED (server pack only)
- UVision LITE (server pack only)
- UVision Server (server pack only)
- Vault Integrations
Mods found NOT to be compromised:
- Fabulously Optimized
Bukkit plugins:
- Anti Command Spam Bungeecord Support
- Anti Redstone Crash (Not to be confused with “NTD AntiRedstoneCrash”)
- Display Entity Editor
- Easy Custom Foods
- Floating Damage
- Fragment Permission Plugin
- Haven Elytra
- Hydration
- MCBounties
- No VPNS
- Simple Harvesting
- The Nexus Event Custom Entity Editor
- Ultimate Leveling
- Ultimate Titles Animations Gradient RGB
Please comment below or email [email protected] if you have new information. We have created this list in hopes of it being helpful from prismlauncher.org and curseforge.com (exact URLs listed below). See above for last update date.
How To Find Out If You Were Infected
Run jar-infection-scanner (limited)
The jar-infection-scanner tool detects if you have any dormant or other infected jar files on your disk.
Link: https://github.com/overwolf/jar-infection-scanner/releases
Limitation: There is currently a problem preventing you from scanning your entire disk or users folder because the program attempts to access protected system files (those were most likely not infected). We have already opened a ticket about this. Until then, use the other tool below or simply only select your Minecraft server folder or your
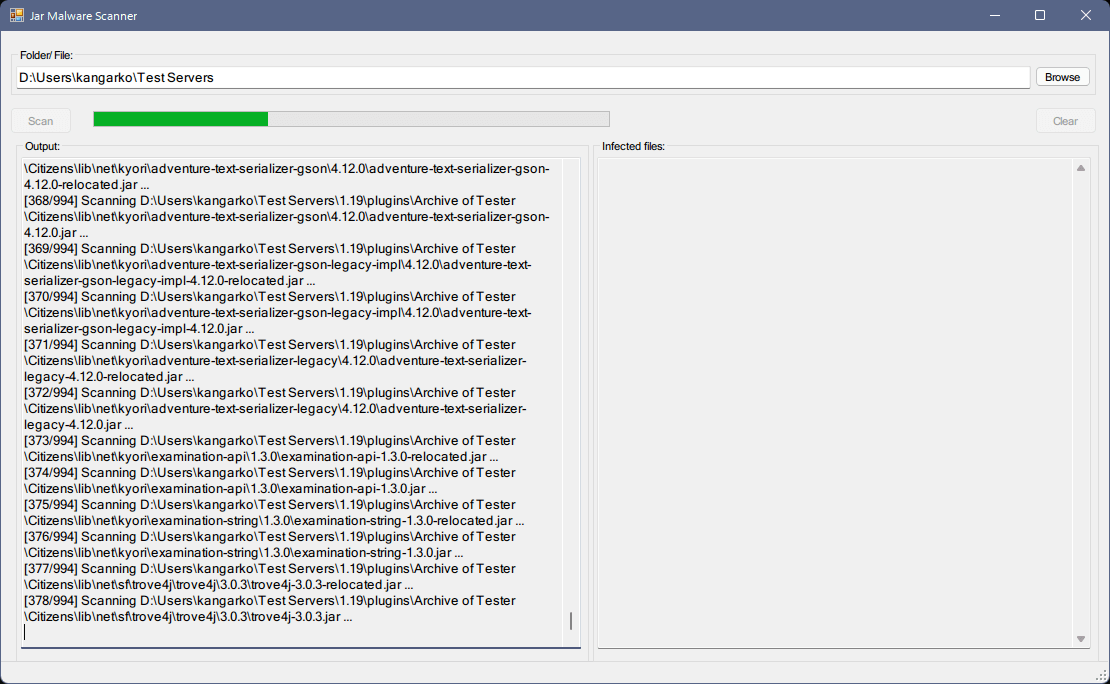
Run nekodetector
This is a powerful tool that will find the malware infection by scanning all jar files on your computer and analyzing them.
Link: https://github.com/MCRcortex/nekodetector/releases
You will need to have a Java SDK installed on your operating system to run this tool and create a launch script.
Usage:
- Download the .jar file and place it inside a new folder such as “detector” on your disk.
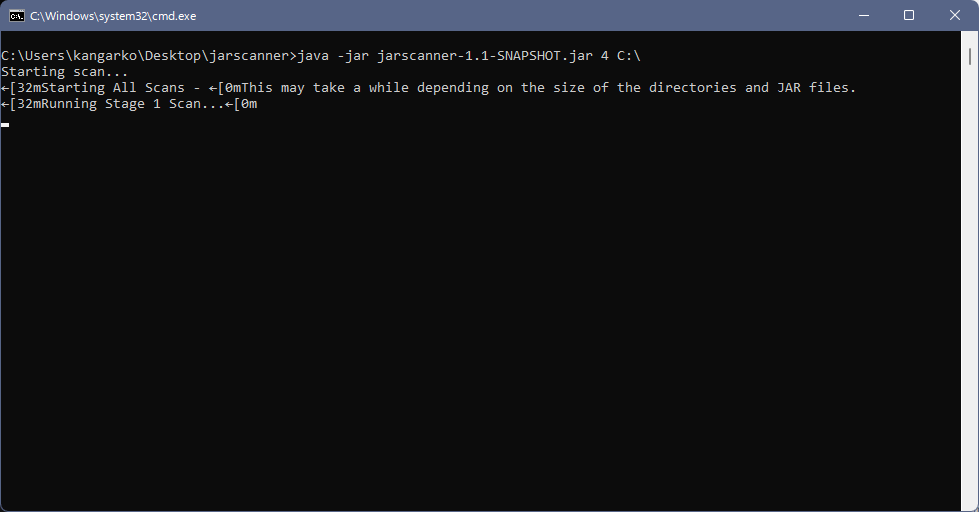
- Create a new .txt file using Notepad, Notepad++, Sublime Text or any plain text editor with the following content:Windows:
java -jar jarscanner-1.1-SNAPSHOT.jar 4 C:\ pause
Linux:
#!/bin/sh cd "$(dirname "$(readlink -fn "$0")")" java -jar jarscanner-1.1-SNAPSHOT.jar 4 /
Replace “jarscanner-1.1-SNAPSHOT.jar” with the name of the downloaded file.
- Replace the .txt file extension with .bat for Windows and with .sh for Linux. For Windows, you will need to have hidden files visible. Click here to learn how. You also need to have file name extensions shown. Click here to see how to show file name extensions.
- Run the tool and pray that you are not infected.
What To Do If You’re Infected
If the above tools detect an infection (or if you simply want to be safe), you need to proceed to check if the malware has spread itself on your disk.
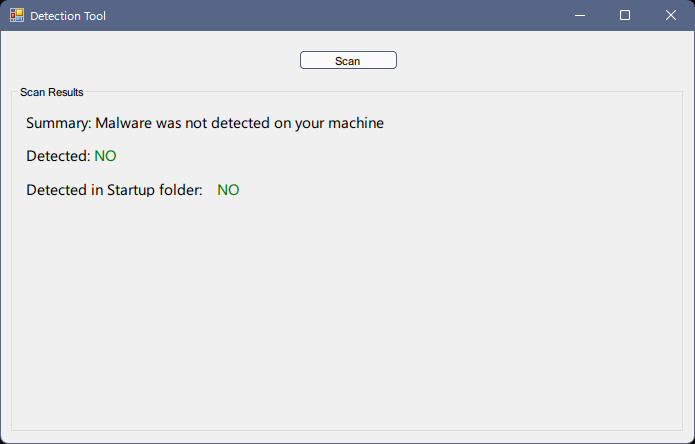
Run detection-tool
This tool will scan your files to see if the malware has already entered its next stage of spread. It will also list the files detected on your computer so you can remove them.
Link: https://github.com/overwolf/detection-tool/releases
Fractureiser Removal Process
Warning: At this time, it is not known to which extent the malware can infect the system and what it can do. The information has been compiled by reverse engineering parts of it but it is not complete. While we will try to keep a track of this, please follow the sources below for updates.
If you find spread out files from the detector-tool on your system, you unfortunately need to assume that everything on your system is compromised.
If you want to be 100% safe, you should:
- Back up anything you do not want to lose when performing a clean wipe on an a flash drive or external disk.
- Using a separate device, change the passwords to all services you were logged into on the old machine (Discord, email, bank, etc.).
- Wipe and reinstall your operating system. There are countless of tutorials on doing this, or simply contact a professional and refer them to this article. If you are creating a bootable ISO, make sure you use a separate device to do that!
Security tips:
- Consider using Two-Factor Authentication for every site that supports it. You can get Authy or any other app on your phone or use SMS to receive the code.
- Advanced: Use a strong firewall with no automatic rules such that every new program makes it block its connection and ask for your permission. For years, I personally used ESET Smart Security which can do this. It is annoying, but I have had never suffered from a bad infection (to which I know of) because of this paranoid antifirewall policy.
Want To Make Your Own Malware Software?
Having tech skills won’t protect you from infections, but it makes you more resilliant. For the last 5 years we’ve been teaching thousands of people how to code in Java, and how to make their own Minecraft plugins.
We have had students create anti-piracy and anti-malware protections from taking the Project Orion training which you can learn more about here. It’s got a full Java training for those of you who never coded before, and it shows you how to build an advanced Minecraft server with custom plugins and your own ideas. Just one promise:
Sources:
https://github.com/fractureiser-investigation/fractureiser
https://prismlauncher.org/news/cf-compromised-alert
https://support.curseforge.com/en/support/solutions/articles/9000228509-june-2023-infected-mods-detection-tool

